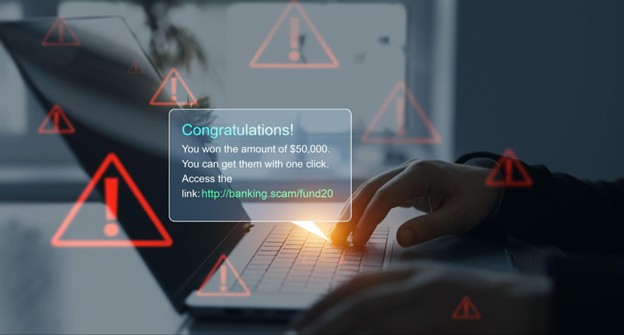
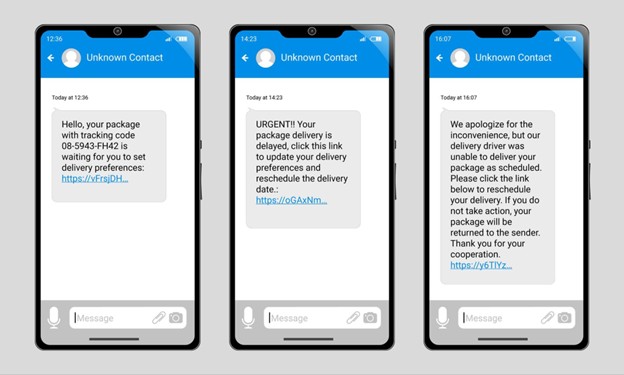
Phishing attacks are one of the most common and dangerous cyber threats facing individuals and businesses today. These scams involve cybercriminals masquerading as legitimate sources, tricking unsuspecting recipients into disclosing sensitive information such as login credentials, credit card details, or personal data. Often containing harmful links or attachments, falling victim to these phishing attacks can result in identity theft, data breaches, and significant financial losses.
To safeguard against these dangers, individuals should remain vigilant in recognizing suspicious emails by looking out for red flags like unfamiliar sender addresses, generic greetings, and urgent requests. Employing security measures such as multi-factor authentication and spam filters can also significantly reduce the likelihood of falling victim. Learn how to spot phishing attempts and safeguard your personal and business information against cybercriminals.
Table of Contents
How to Identify and Prevent Phishing Attacks
The Mechanics of Phishing Attacks
Types of Phishing Attacks
Email Phishing
Spear Phishing
Whaling
Vishing
Smishing
Effective Prevention Strategies Against Phishing Attacks
1. Utilize Spam Filters
2. Implement Multi-Factor Authentication (MFA)
3. Regularly Update Software
4. Educate Employees
5. Employ Cyber Security Services
6. Use AI-Powered Security Solutions
7. Report Phishing Attempts
Don’t Let Phishing Attacks Compromise Your Data
The Mechanics of Phishing Attacks
Phishing typically involves sending emails or messages masquerading as legitimate entities. Upon opening a phishing email, users may be urged to click on malicious links or provide personal details, such as login credentials or credit card numbers. Attackers often create a false sense of urgency, encouraging recipients to act quickly without thoroughly analyzing the content. This tactic effectively manipulates users, making them more likely to engage with the harmful message. To counter these deceptive tactics, many organizations invest in robust cyber security services that help detect and block phishing attempts before any harm is done.
Examples of phishing messages commonly include notifications about account issues or enticing offers that seem too good to pass up. Often, these messages originate from phishing scammers posing as trusted companies to gain credibility. If users fall victim to the bait, they risk identity theft, serious data breaches, and significant financial loss.
Types of Phishing Attacks
Phishing comes in many forms, with cybercriminals using a range of tactics tailored to exploit their victims’ instincts. Understanding these types of phishing attacks can empower individuals and organizations to recognize threats and implement effective measures to prevent phishing attacks. Leveraging AI-powered security can further enhance detection and prevention by automatically identifying suspicious patterns and blocking malicious activity in real time.
Email Phishing
Email phishing stands as the most common and straightforward method, targeting a broad audience with carefully crafted messages. These phishing emails often mimic legitimate companies—usually recognizable brands or financial institutions—to create a false sense of trust. As you open such emails, you may notice urgent calls to action, like verifying your account or claiming a prize. The intent is clear: to trick users into clicking on malicious links or downloading attachments that contain harmful software.
- Generic Greetings: Phrases like “Dear Customer” instead of your name.
- Suspicious URLs: Links that don’t lead to the expected domain.
- Urgency: “Your account will be suspended unless you act now!”
Awareness of these red flags can help combat phishing scams effectively. Engaging in regular training and utilizing spam filters can assist in identifying and blocking these emails.
Spear Phishing
Spear phishing involves targeted attacks aimed at specific individuals or organizations. Unlike generic phishing emails, spear phishing messages often include personal information collected from social media or previous interactions. This attention to detail makes such messages appear more credible and increases the likelihood of the recipient falling victim.
- Personalized Content: Use of your name, title, and references to previous communications.
- Familiar Senders: Emails appearing to be from colleagues or business partners.
This tactic thrives on deception, causing individuals to disclose sensitive information. Organizations can utilize cyber security services to enhance employee awareness and training focused on recognizing such tailored attacks.
Whaling
Whaling is a subtype of spear phishing that specifically targets high-profile individuals, such as executives or other key decision-makers within a company. Attackers often use urgent requests that exploit the authority and responsibilities associated with these roles to obtain sensitive company data.
- High-Stakes Requests: Emails claiming to require immediate action regarding significant financial transactions or sensitive projects.
- Spoofed Emails: Messages that appear to come from legitimate accounts of trusted sources.
With executives being prime targets for phishing scams, businesses must employ stringent security measures, including multi-factor authentication and secure email gateways, to protect against these sophisticated attacks.
Vishing
Vishing, short for voice phishing, employs telephone calls to extract sensitive information. In this format, attackers impersonate legitimate organizations, claiming issues that require immediate attention. For example, a caller may pose as a bank representative, asking you to verify account details due to suspicious activity.
- Pressuring Tactics: Urging you to provide information quickly without time to verify legitimacy.
- Unsolicited Calls: Receiving calls from numbers you do not recognize, especially those claiming to be your bank or service provider.
Training employees to report suspicious calls and promoting awareness about the risks associated with vishing can help mitigate this threat.
Smishing
Smishing involves sending fraudulent SMS messages that mislead recipients into clicking on malicious links or providing personal information. Like other phishing methods, the aim is to create a sense of urgency or importance to encourage quick actions.
- Links in Text Messages: Shortened URLs or prompts to click for account verification.
- Promotional Offers: Unsolicited messages claiming you’ve won a prize or a special deal.
To combat smishing attacks, individuals should be encouraged to verify any unknown messages and utilize anti-malware software to protect mobile devices from malicious downloads.
Effective Prevention Strategies Against Phishing Attacks

Phishing attacks present significant risks, making it critical to implement robust prevention strategies that enhance security. Phishing attacks often employ deceptive tactics to trick users into revealing personal data, making them one of the most prevalent forms of cybercrime today. Cybercriminals send phishing messages designed to mimic legitimate communications, leading victims to click on malicious links or divulge login credentials. This can result in identity theft and severe data breaches, underscoring the need for robust protective measures. Combining technology, training, and proactive measures can significantly reduce the likelihood of falling victim to these cyber threats. Here are several key strategies to help prevent phishing attacks effectively.
1. Utilize Spam Filters
Spam filters are the first line of defence against phishing emails. These tools automatically identify and block malicious messages before they reach your inbox, reducing exposure to phishing attempts.
- Spam filters analyze incoming emails for known phishing characteristics, such as suspicious hyperlinks or problematic sender addresses.
- Utilizing advanced spam filtering solutions increases the likelihood of filtering out phishing messages, keeping your inbox cleaner and safer from malicious links.
2. Implement Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds an essential layer of security to your login processes. Even if a phishing attack compromises your login credentials, MFA can prevent unauthorized access.
- MFA requires users to provide two or more verification factors to gain access to their accounts, making it much harder for attackers to succeed even if they have stolen passwords.
- This strategy not only combats identity theft but also protects sensitive information by ensuring that only authorized users can access critical systems.
3. Regularly Update Software
Keeping software and anti-malware solutions up-to-date is vital in safeguarding your devices. Cybercriminals often exploit known vulnerabilities in outdated software during cyber attacks.
- Frequent updates patch security flaws that phishers might target, thus reducing the risk of downloading malware from malicious websites.
- Regularly updated systems bolster your overall security measures and contribute to maintaining a secure operational environment.
4. Educate Employees
Employee training is fundamental in creating a culture of cyber awareness. Ensuring that team members can recognize phishing scams is crucial to reducing the chances of falling victim to phishing attempts.
- Training staff on identifying suspicious emails and understanding common phishing tactics empowers them to make informed decisions and report phishing attempts promptly.
- Engaging training sessions can cover real-life examples of phishing attacks, helping employees learn how to spot potential threats.
5. Employ Cyber Security Services
Partnering with cybersecurity services can greatly enhance your organization’s defences against phishing campaigns. These experts can evaluate your existing security measures and design a tailored plan.
- Professional services offer insights into current vulnerabilities and can implement monitoring tools that detect phishing in real time.
- They can also conduct regular assessments to ensure that your systems remain resilient against evolving threats.
6. Use AI-Powered Security Solutions
Leveraging AI-powered security can revolutionize your approach to threat detection and prevention. AI technologies analyze user behaviour patterns to identify anomalies that may indicate phishing.
- AI solutions can recognize suspicious activity and flag potential phishing messages or attempts, greatly enhancing threat detection capabilities.
- By analyzing vast amounts of data, AI can adapt to new phishing tactics, keeping your organization one step ahead of cybercriminals.
7. Report Phishing Attempts
Establish a clear process for reporting phishing attempts within your organization. Encourage employees to report any suspicious emails or communications immediately.
- Prompt reporting allows your IT team to investigate potential threats quickly, reducing the impact on sensitive data and minimizing the risk of data breaches.
- Maintaining awareness of reported phishing attempts helps your organization stay informed about emerging phishing tactics and trends.
Implementing effective prevention strategies is essential to combat the ever-evolving threat of phishing attacks. By combining advanced tools like spam filters and AI-powered security with thorough employee training and robust cyber security services, organizations can significantly enhance their defence against these deceptive tactics.
Don’t Let Phishing Attacks Compromise Your Data
Your sensitive data is too valuable to leave unprotected. As phishing scams become more sophisticated, knowing how to identify and prevent these threats is essential. Implementing security measures like multi-factor authentication, anti-malware software, and regular software updates will help keep your data safe. Proactive strategies and the right tools make it harder for cybercriminals to succeed. Leverage professional cybersecurity services to defend against phishing emails, malicious websites, and other cyber threats, with advanced detection and rapid incident response to protect your business and personal information.